Function overview
Hiperlinx ’s Active Directory security services recognize that AD is inherently complex, often managed by different administrators over time, each with their own methods. This diversity in management approaches makes AD susceptible to misconfigurations and gaps, which traditional auditing methods may not adequately address. This is where we excel. Our AD security in-depth audit uncovers these weaknesses and offers precise security mitigation strategies to address them effectively.

The Advantage
Hiperlinx Active Directory Security Assessment typically discovers more high priority findings than commercial tools. We use manual enumeration along with in-depth analysis to discover, identify, and provide feasible, actionable recommendations to get issues fixed.
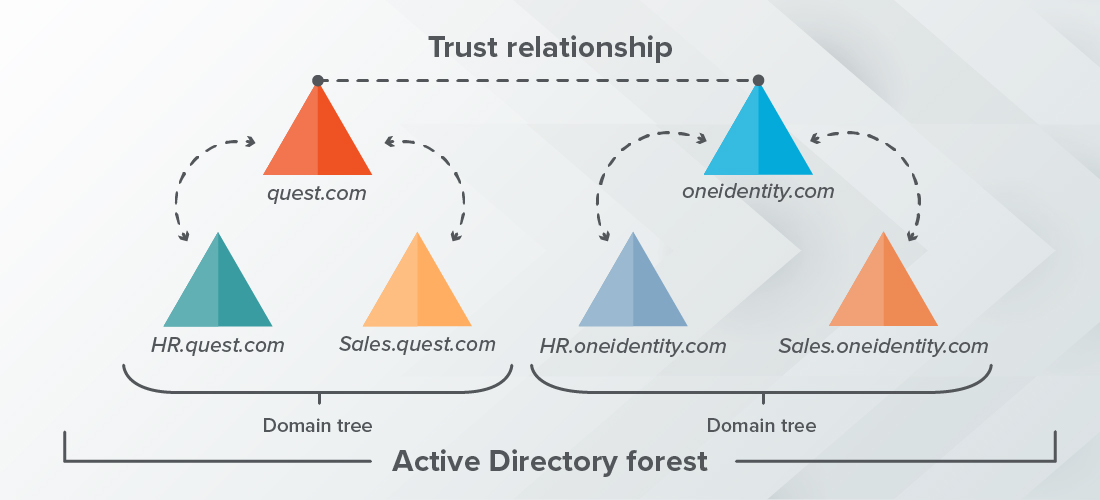
Key Security Assessment Components

What you get in our AD Report
Active Directory Security Assessment Findings & Recommendations
- Most significant findings
- Potential Attack Paths
- Top Recommended Remediation Items

